
The Spread of Online Dangers Since Lockdown
During the coronavirus emergency lockdown, the internet has been transforming the way we interact, do business and go about our everyday life.But the worldwide web has always been a sea that harbours many sharks, and like the pathogen we are…
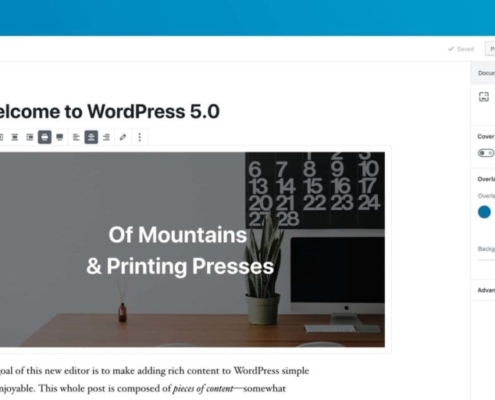
Word up! Tickbox technical director Daryl Phillips explains recent changes to WordPress and Tickbox’s approach to upgrading your site
It’s been a week (or so) since WordPress 5.0 (Bebo) was released. Some of you may have seen, upgraded or received an update notification about it.
It's the biggest update so far for Wordpress. The main focal point centred around the rich…
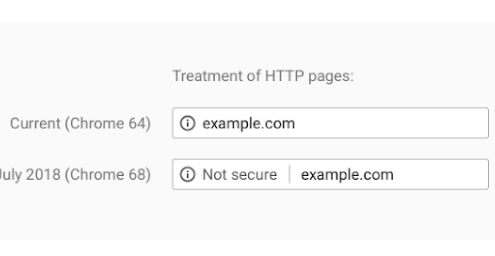
Google security changes mean you may need an SSL certificate
Changes to how Google Chrome treats standard HTTP websites mean that sites which collect any form of data - even simple contact forms or site search - will need a security certificate or risk being labelled as "not secure".
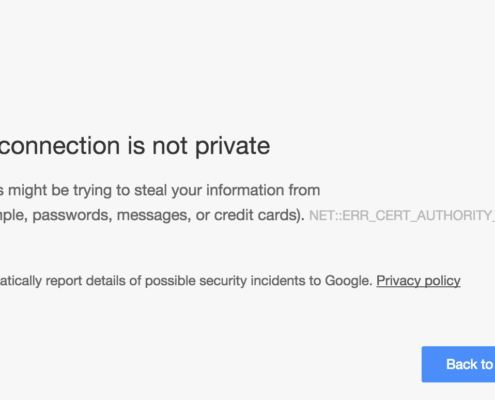
Goodbye SHA-1, Hello SHA-2
Google Chrome (and similarly FireFox) is deprecating support for SHA-1 before the year is out. So the time to check and upgrade is paramount. All SHA-1 support will be removed by the end of 2016. Your site will continue to be served, but with that unruly error: "Your website is not trusted.".

DirtyCow moooo-ving to a server near you
No you read that right. DirtyCow - or copy-on-write for those inclined - is the latest hidden vulnerability to hit unprotected servers and in some cases Linux driven smartphones.

Attack of the botnets – what can you do to keep your WordPress site safe
If you have a WordPress site, its probably being attacked by hackers right now. In fact industry research suggests that there are more than 3,300 automated bots attempting to access any given WordPress site at any time.
Does that mean WordPress isn't secure? No - WordPress is simply the world's most popular website development platform. Sites build on other platforms will be attacked too, but the sheer number of WordPress sites means the figures add up.
So what can you do about it?
